
ACCESS CONTROL AND JOINT MANAGEMENT FOR
COLLABORATIVE PEER GROUPS
Wenhua Qi
School of Electronic and Information Engineering , Beihang University, Xueyuan Rd., Haidian District, Beijing, China
Keywords: Peer groups, Access control, Joint management, JXTA technology.
Abstract: Collaborative peer groups means that multiple self-organizing peers aggregating in a controlled manner to
accomplish some collective goals. Peer groups share the properties of peer-to-peer overlay network, includ-
ing full decentralization, symmetric abilities, and dynamism, which make security problems more compli-
cated. Most prior work focused on authentication, group key management and communication security.
However, access control is an important precondition of many security services. Intend for a pure decentral-
ized model without centralized server, our framework employs a distributed delegation authorization
mechanism and proposes an authority selection scheme. Multiple authorities could exist in this design,
which could avoid single point of failure. Based on the role-based trust management language RT, this pa-
per presents an attribute-based access control framework, and describes a formal joint authorization protocol
under voting scheme, to satisfy security requirements of multiple peers. We also introduce our implementa-
tion experience by applying JXTA technology.
1 INTRODUCTION
In some cases, multiple self-organizing peers aggre-
gate in a controlled manner, and use multiway com-
munication primitives to accomplish their collective
goals. Collaborative peer groups (Sunderam, 2003.
Gong, 2002) is introduced to refer to such peer-to-
peer networks, which are a strong and flexible struc-
ture to enable coordination between applications,
server-client, and peers in networks. Group settings
may be synchronous or asynchronous manner, and
communication models vary from one-to-many or
few-to-many to any-to-any.
Collaborative Peer groups share the properties of
peer-to-peer overlay network, including full decen-
tralization, symmetric abilities, and dynamism,
which make security problems more complicated.
Most prior work has been done in the context of
group membership authentication, group key man-
agement (Rodeh, 2000), and communication secu-
rity. However, access control is an important pre-
condition of many security services. Conventional
group access control mechanisms make authoriza-
tion decisions based on the identity of requester,
such as Gothic (Judge, 2002), Intergroup (Agarwal,
2001). Unfortunately, in distributed environments,
members often are unknown to one another; access
control based on identity may be ineffective.
Upon the analyses, distributed authorization and
access control mechanisms need to be implemented
in collaborative peer groups. To avoid single point
of failure and enhance scalability of the system, in-
stead of using a centralized model (Judge, 2002), we
employ a distributed delegation authorization
mechanism and propose an authority selection
scheme. Multiple authorities could exist in this de-
sign, reducing both the overhead and the response
time of group authority. Based on the role-based
trust management languages RT (Li, 2002), our
work presents an attribute-based access control
framework and describes a formal joint authoriza-
tion protocol under voting scheme, to satisfy secu-
rity requirements of multiple peers. By applying
JXTA technology, we also introduce our implemen-
tation architecture and experience.
2 AUTHORITY SELECTION IN
PEER GROUPS
Intend for a fully distributed peer group without cen-
tralized control over group membership, our frame-
work presents that a peer within the group could
83
Qi W. (2006).
ACCESS CONTROL AND JOINT MANAGEMENT FOR COLLABORATIVE PEER GROUPS.
In Proceedings of the International Conference on Security and Cryptography, pages 83-86
DOI: 10.5220/0002099200830086
Copyright
c
SciTePress

propagate its own attributes to other peers. We pro-
posed a quality model based on a set of quality crite-
ria. For each criterion, we provide a definition, indi-
cate its granularity, and provide rules to compute its
value for a given peer. Thus, an authority will dele-
gate its authority property to a neighbor which has
high quality criteria. This allows the new peers to
accept new member into the peer group, reducing
both the overhead and the response time of author-
ity.
2.1 Peer Group Quality Model
To differentiate the peers of a group during authority
selection, their non-functional properties need to be
considered. We consider five generic quality criteria
for each peer: (1) cost (2) capacity, (3) age, (4)
global trust value, and (5) neighbor link value.
Cost: Given a service to a peer i, such as relay ser-
vice, we define cost as the resource cost of a service
provider has to pay for providing the service.
Capacity: We define capacity as the ability of a peer
to process and relay queries and query responses.
Age: We define age as the length of time up to now
since a peer joins the network up to present.
Trust: We may adopt the trust model EigenRep
(Kamvar, 2003) and define trust as the global trust
value of a peer.
Link: Peers also regularly link to other peers. We
define link as the number of links from i that can
reach after at most one indirection.
Given the above quality criteria, the quality vector
of a peer i is defined as follows.
Q(i)=(Price
i
, Capacity
i
, Age
i
, Trust
i,
, Link
i
)
2.2 Authority Selection by
Optimization
In our approach, when the group members increase,
the authority peer collects information about the
QoS of its neighbors, and a quality vector is com-
puted for each of the peers. Based on the quality
vectors, a peer with high quality criteria will be se-
lected as the authority peer. This selection process is
based on the weight assigned by the authority to
each criterion, and a set of policy-defined constraints
expressed using a simple express language. Exam-
ples of constraints that can be expressed include ca-
pacity constraints and trust constraints. By merging
the quality vectors of all these n neighbors, a matrix
Q=(Q
i,j
;
1;15in j≤≤ ≤ ≤
) is built, in which each
row Q
j
corresponds to a peer while each column cor-
responds to a quality dimension. A Simple Additive
Weighting (SAW) (L, 1981) technique is employed
to select authority peers in this design, including two
phases:
1. Scaling Phase. Some of the criteria could be nega-
tive, i.e., the higher the value, the lower the quality,
such as Cost. Other criteria are positive, i.e., the
higher the value, the higher the quality, such as Ca-
pacity. For negative criteria, values are scaled ac-
cording to
max
,
,
max min
j
ij
ij
jj
QQ
V
QQ
−
=
−
. For positive criteria,
values are scaled according to
min
,
,
max min
ij j
ij
jj
QQ
V
QQ
−
=
−
.
2. Weighting Phase. The following formula is used
to compute the overall quality score for each
neighbor:
5
,
1
() ( )
iijj
j
Score peer V W
=
=∗
∑
(0 ≤ Score (peer
i
)
≤
1)
where W
j
∈
[0, 1] and
5
1
1
j
j
W
=
=
∑
. W
j
represents
the weight of criterion j. The authority expresses
their preferences regarding QoS by providing values
for the weights W
j
.
3 JOINT MANAGEMENT
This section presents a role-based trust model and
joint authorization protocol to satisfy the access con-
trol requirement of peer groups.
3.1 Access Control Policy
In a fully distributed group, our framework adopts
credential in trust management (Li, 2002) as authen-
tication method. Role is defined as A.r(h
1
, " ,h
n
),
where A is entity name,r is role name. A Role may
include zero or more restriction parameters h
i
. Ac-
cess Policy has the form of
12
rr<←, vote>, where
12
rr
←
is access rule. When a peer requests the role
of r
1
, the policy statement is checked. vote has one
of the following forms:
1) true: vote is always true;
2) fixed(r, m, f): A voting is called among members
of the r role. If k votes are received and f
×
k are yes,
then vote is true(m, k
∈
integer; k ≥ m; f∈ [0,1]).
3) dynamic(r, f
1
, f
2
): This is equivalent to fixed(r,
SECRYPT 2006 - INTERNATIONAL CONFERENCE ON SECURITY AND CRYPTOGRAPHY
84
m=n
×
f
1
, f
2
), where the role r has n members(m,
k
∈ integer; f
1
, f
2
∈ [0,1]).
3.2 Joint Authorization
The joint authorization protocol based on JXTA
technology has five phases, which are group initiali-
zation, searching group advertisement, authoriza-
tion request, voting, and PGC issuance.
1) Group Initialization. The group authority peer
initializes the local secure environment by creating a
secure peer group, and then publishes the secure
peer group advertisement into the network. The
group adv. contains access control policy of peer
groups and various parameters such as group name,
voting type, etc.
2) Searching Group Advertisement. When a new
peer wants to join the group, it must firstly obtain
the advertisement of its attributive peer group. In
this design peers have two ways to get this informa-
tion. Peers may discovery the authorization service
advertisement from the rendezvous peer or by flood-
ing.
3) Authorization Request. Having the advertise-
ment message, new coming peer may connect with
the corresponding authority peer. The new peer will
generate a group certificate issuance request contain-
ing its desired privileges.
4) Voting. Upon receipt of authorization request, the
authority peer first verifies the signature. In a fully
distributed peer group, the request is either accepted
or rejected by the collective set of current members.
The authority peer then propagates the request to
call a vote of peers. According to the policy, multi-
ple peers authenticate the attribute of a requester,
vote, and reply with a signed message to approve or
reject the authorization request.
5) PGC Issuance. Once enough votes are collected,
the authority verifies all the votes, and decide
whether to accept the new node as a member. If the
requester is qualified, the authority will issue the
group certificate to it and update the related peer
group information. Then, the new node can join the
secure peer group.
4 IMPLEMENTATION
We implemented the distributed access control in
peer-to-peer collaborative systems using Java pro-
gramming language. The communication facility
among peers is provide by JXTA(Sun, 2002.
Altman, 2003), an overlay network middleware
messaging system. The measurements are performed
on 32 nodes with a high-speed LAN, and each node
is the Intel Nocona Xeon 2.8GHz, 2G RAM Linux
machine. As the setup phase of the peer group, the
Group Authority creates and publishes the group au-
thorization service advertisement. All group access
control protocol messages are encapsulated within
standard JXTA messages. To satisfy the distributed
authorization requirement and balance the group au-
thority overhead, the group authority will republish
the authorization service advertisement after delegat-
ing the authority attribute to another group member.
The group authorities may receive multi-requests
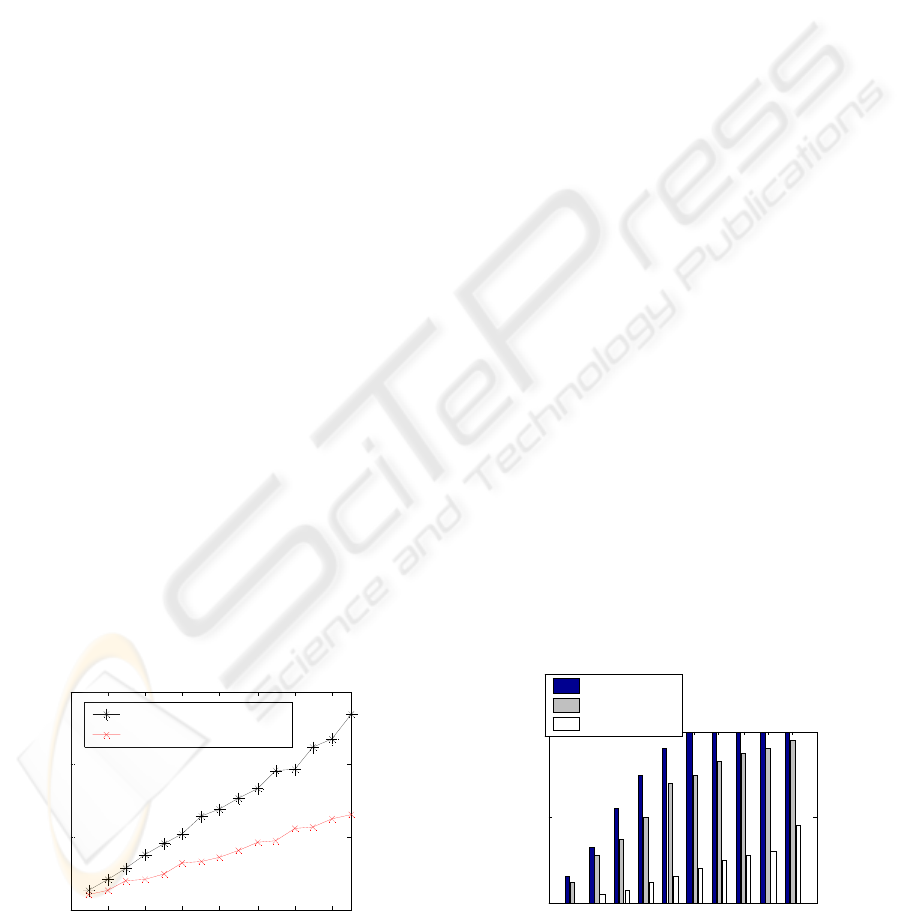
in a short time interval. Figure 1 shows the average
join coat for the centralization and delegation. The
number of current group members is 30, and the
threshold is 30%. In Figure 2,we plot the accumu-
lated joining ratio against time, and contrast differ-
ent authorization approaches with 40 new nodes. We
can see that after 20 seconds, the success joining ra-
tios vary from 12.5% for a centralized scheme, 50%
for two authorities, to 75% for three authorities.
0 4 8 12 16 20 24 28
0
10
20
30
Join Group Requesters (n) threshold=30%
Average Join Time (seconds)
centralization authority
delegation authority
5 10 15 20 25 30 35 40 45 50
0
50
100
Time
(
seconds
)
Accumulated joining ratio(%)
Group GA =3
Group GA =2
centraliztion
Figure 1: Average Join Cost of Dynamic Requesters. Figure 2: Average Join Cost of Dynamic Requesters.
ACCESS CONTROL AND JOINT MANAGEMENT FOR COLLABORATIVE PEER GROUPS
85

5 RELATED WORK
Many researches have been accumulated on security
in multicast groups. Gothic (Judge, 2002) provides
security service for IP-Multicast. An external access
control server performs authentication and authori-
zation based on PKI certificates. The Antigone
(McDaniel, 1999) utilizes a centralized access con-
trol approach in which member access is mediated
by a Session Leader.
Sconce(Kim, 2003) presents an admission control
framework in peer groups, which treats peer groups
as a flat structure where all peer nodes have identical
rights and responsibilities. Thus Sconce, which lacks
the attribute of peers, can not simplify authorization
in collaborative environments. JXTA presents a se-
curity mechanism also based on PKI certificates
(Altman, 2003). Intergroup (Agarwal, 2001) pro-
vides access control by using an authorization ser-
vice, Akenti (Thompson, 2003), which provides a
coarse granularity for access control.
Most of the systems described above provide ac-
cess control based on identify of participants, in-
stead, this paper adopts attribute-based access con-
trol in group. Based on the RT languages (Li, 2002),
our work presents a fine-grained access control
framework for collaborative peer groups. Mean-
while, based on the policy model, this paper empha-
sizes the need of joint management for peer groups.
Joint authorization efficiently provides security for
communication and data resources shared by multi-
ple peers.
6 CONCLUSION
This paper presents a fine-grained and attribute-
based access control framework for collaborative
peer groups. We propose a distributed delegation
authorization mechanism to avoid single point of
failure. In order to simplify authorization and access
control in collaborations, access control decisions
are made based on authenticated attributes of the
peers, which improve flexibility of decentralized au-
thorization. By applying JXTA technology, this pa-
per describes a formal joint authorization protocol
under voting schemes, to satisfy security require-
ments of multiple peers.
REFERENCES
Sunderam, V., Pascoe, J., Loader, R., 2003. Towards a
Framework for Collaborative Peer Groups. In the 3rd
IEEE/ACM International Symposium on Cluster Com-
puting and the Grid.
Gong, L., 2002. Project JXTA: A Technology Overview.
from http://www.jxta.org/project/www/docs/
TechOverview.pdf.
Rodeh, O., Birman, K., Dolev, D., 2000. Using AVL
Trees for Fault Tolerant Group Key Management.
Technical Report 2000-1823, Cornell University,
Computer Science.
Judge, P., Ammar, M., 2002. Gothic: A Group Access
Control Architecture for Secure Multicast and Any-
cast. In INFOCOM.
Agarwal, D., Chevassut, O., Thompson, M., Tsudik, G.,
2001. An Integrated Solution for Secure Group Com-
munication in Wide-Area Networks. In the 6th IEEE
Symposium on Computers and Communications.
Li, N., Mitchell, J., Winsborough, W., 2002. Design of a
Role-Based Trust Management Framework. In the
IEEE Symposium on Security and Privacy.
Kamvar, S., Schlosser, M., 2003. EigenRep: Reputation
Management in P2P Networks. In the Twelfth Interna-
tional World Wide Web Conference.
L, H., Yoon, K., 1981. Multiple Criteria Decision Making.
Lecture Notes in Economics and Mathematical Sys-
tems.
Sun Microsystems Project JXTA v2.0: Java Programmer's
Guide. 2002, from http://www.jxta.org/.
Altman, J., 2003. Sun Microsystems, Project JXTA: PKI
Security for JXTA Overly Networks. from
http://www.jxta.org/docs/pki-security-for-jxta.pdf.
McDaniel, P., Prakash, A., Honeyman, P., 1999. Anti-
gone: A Flexible Framework for Secure Group Com-
munication. In the 8th USENIX Security Symposium.
Kim, Y., Mazzocchi, D., Tsudik, G., 2003. Admission
Control in Peer Groups. In the IEEE International
Symposium on Network Computing and Applications.
Thompson, M., Essiari, A., Mudumbai, S., 2003. Certifi-
cate-Based Authorization Policy in a PKI Environ-
ment. ACM Transactions on Information and System
Security.
Nita-Rotaru, C., Li, N., 2004. A Framework for Role-
Based Access Control in Group Communication Sys-
tems. In the International Workshop on Security in
Parallel and Distributed Systems.
SECRYPT 2006 - INTERNATIONAL CONFERENCE ON SECURITY AND CRYPTOGRAPHY
86
