
EFFICIENT INFORMATION ACCESS FROM CONSTRAINT
WIRELESS TERMINALS
Exploiting Personalization and Location-Based Services
Hans Weghorn
Faculty for Information Technology, BA-University of Cooperative Education, Rotebühlplatz 41, Stuttgart, Germany
Keywords: Personalization, Wireless Internet, Wireless JAVA, Location-based Services, Information Management
Abstract: Today, the success of data services used from small mobile devices, like digital phones or PDAs, appears
very limited. Different reasons can be identified, which prevent the average customer from broadly using
wireless data services. At first, the user has to deal with very uncomfortable devices in terms of UI
ergonomy, and on the other hand, the costs for wireless data communication are extremely high. These
restrictions can be overcome by employing a system concept, which is built up on two main components: A
personalized display software allows simplifying the information access on the wireless terminal, while an
intermediate agent residing on the Internet takes care of mining the desired contents from the open Web. In
addition to the improved UI handling, this concept offers a reduction of access costs and an increase in
retrieval speed. Real-world experiments with an information system on actual train departures are reported
for measuring and demonstrating the benefit of the described system concept.
1 INTRODUCTION
Up to now, a common use of data services accessed
from mobile terminals could not establish very well.
Due to their broad market distribution, digital
mobile phones for cellular networks would yield a
very interesting platform for data services, e.g.
information retrieval on traffic situation on lanes and
public transportation. Unfortunately, the user of
these devices today faces a couple of constraints,
which prevent a wide acceptance of such wirelessly
accessed data services.
Considering first the handling of mobile devices,
it has to be stated that software tools are usually very
uncomfortable. Most tools do not sufficiently respect
the constraints of small mobile devices
(Johnson, 1998), because the user often has to enter
information, e.g. lengthy Web paths, account
information, or selection information. The costs for
the wireless transfer of data contents represent
another critical aspect. For instance in Germany, a
comparison of the tariffs of land line networks (e.g.
ADSL technology) and cellular phone networks
shows that transferring data amounts wirelessly is
roughly 10
4
times more expensive.
Furthermore, the wireless data rates are slower in
the order of 10
2
– 10
3
. WLAN (Riezenmann, 2002)
seems to be an alternative wireless access
technology, which can overcome these back draws.
Unfortunately, it is not truly feasible for a seamless
information retrieval, because it does not supply
roaming and requires more complicate hardware.
E.g., a laptop computer linked to a WLAN hot spot
is good for reading e-mails in a restaurant or at an
airport terminal, but it cannot conveniently be used
for accessing current departure information on, e.g.,
trains or planes while walking or traveling to the
station or airport.
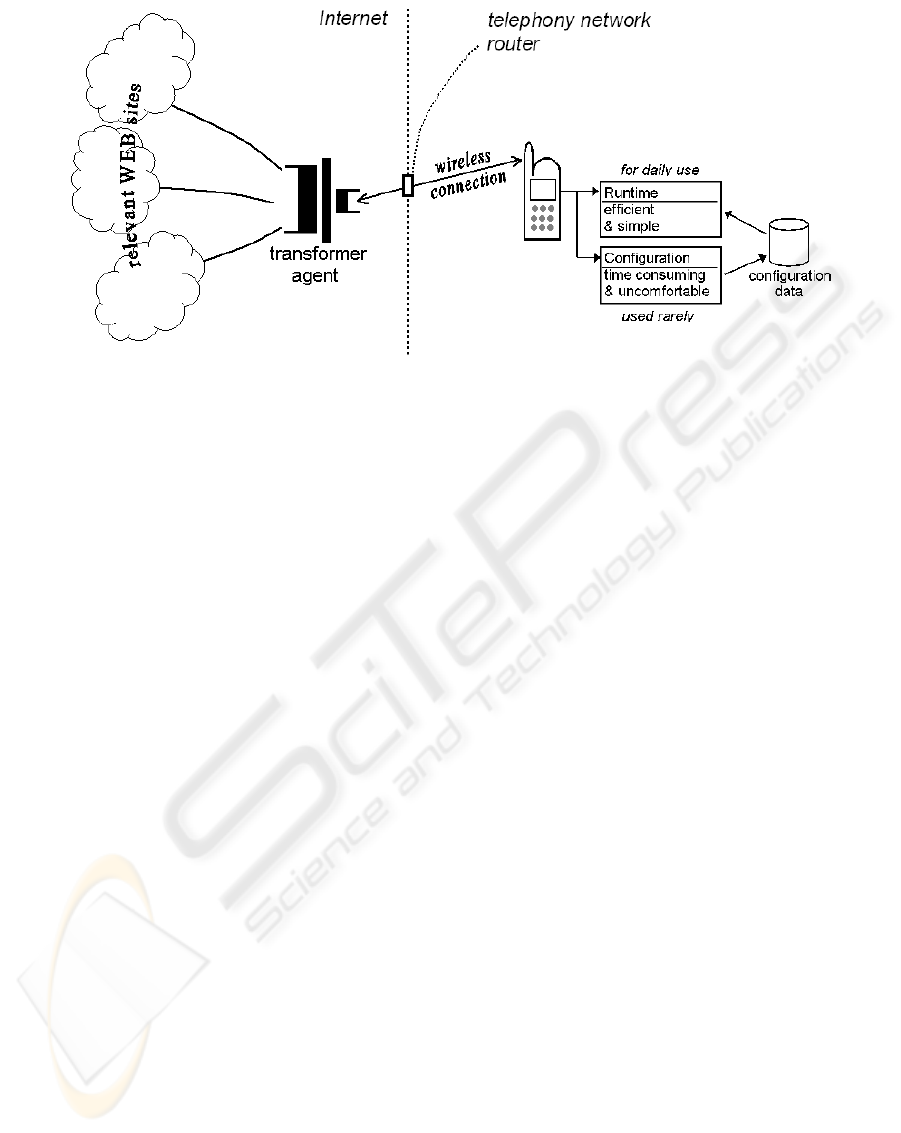
A system concept, which was developed and
reported during the recent years (Weghorn, 2003;
Weghorn, 2004-1), is presumed to overcome these
restrictions. The concept bases on two components
(Fig. 1): One part is personalized display software
for the wireless terminal, which minimizes the
required inputs from the user and which optimizes
the presentation of the results. And the other part is a
data-mining agent running on a central server on the
Internet, which appropriately collects, examines and
prepares the desired information content for a
transfer to the wireless display terminal, as soon as
the user remotely commands this. Since this system
collects customer specific contents on base of
customized tools, the name C2C was defined for this
mechanism.
223
Weghorn H. (2005).
EFFICIENT INFORMATION ACCESS FROM CONSTRAINT WIRELESS TERMINALS - Exploiting Personalization and Location-Based Services.
In Proceedings of the First International Conference on Web Information Systems and Technologies, pages 223-230
DOI: 10.5220/0001236202230230
Copyright
c
SciTePress
The user interacts with the C2C information
retrieval system through the wireless terminal (Fig.
1). During this, the terminal executes specialized
display software, which directs information queries
to a central service agent residing on the Internet.
The display software has to be constructed in the
following manner:
The required user input actions have to be
minimized.
The results have to be output in a reasonable
presentation.
Preferences of the user (e.g. passwords, account
information) have to be remembered
automatically, or should be editable by the user.
The terminal software retrieves the desired
information from the Internet agent by its
activation with the appropriate settings and user
preferences
The counterpart to the display tool is the mining
agent. The agent has to be permanently available on
the Internet, and it is in charge of sourcing the
addressed contents – in many cases from the open
Web. For instance, there exist many Web sites,
which provide current information on traffic
situation on highways and other main routes, and
these could be used for a traffic information system.
As other example, a mining agent could be
employed to collect e-mail messages (or concise
parts of it) for a remote display.
This kind of middleware should be a more
generalized approach than wrapper or mediator
services, which were reported earlier (Mahmoud,
2002; Wang et al., 2003), because in the new
concept here the mining agent sources information
from different sites in parallel, and retrieves by that
a measure of the quality of information (Weghorn,
2004-2). Depending on the situation, the agent can
already decide which information finally should be
the correct one. In the end, the user will receive on
the terminal the desired output together with a
reliability score.
Clearly, for many cases, the user could do the
same actions through WAP browsing manually, but
of course, the automation of these procedure speeds
up the information access, reduces the access costs,
offers the user a very compact and efficient
handling, and allows finally an appropriate display
of the querying results. The fully programmed
solution (instead of the manual use of standard tools
like WAP browsers) allows also to apply compacted
coding schemes on the expensive and slow wireless
data link between the mobile terminal and the
mining agent, which should additionally increase
access speed and the effect of cost saving. In the
reports about the different development stages of the
C2C concept (Weghorn, 2004-1) the investigations
mainly were derived from computer simulations of
the wireless access. A considerable advance of this
research presented in the following sections here is
an extended real-world application for a specific
information access system on public transportation.
2 KEY TECHNOLOGIES FOR
EFFICIENCY IMPROVMENTS
2.1 Personalization
Personalization can be used as key for simplifying
the user handling of wireless terminals. For instance,
if the user wants to access e-mail from a handheld
device, all account information (server settings, user
name and password, filter definitions for mail
retrieval) need to be entered only once into the
terminal software, and these settings can be used
Figure 1: Construction concept of the customized information service
WEBIST 2005 - WEB INTERFACES AND APPLICATIONS
224
automatically from this point. After initial
configuration, the user can launch the e-mail
inspection efficiently by pressing only a few buttons
or – depending on the capabilities of the terminal –
even by one single press of a so-called hot key. This
concept renders possible, because handheld devices
usually are treated as personal belongings. This
means that a mobile phone rarely is lent to a
colleague or another person, and hence, the
information on these mobile devices can be
considered as protected contents.
People, who are daily commuting between their
living home and their working place (office, school
place, University, or similar) are also prospective
candidates for using this kind of personalized
information systems, because most societies today
face continuous traffic problems in terms of delays
of public transportation or traffic jams. For a person,
who is using public transportation like trains, the
information query parameters, which have to be
defined once, would be the departure, changing and
destination stations, and probably the kind of train
that is used. Another person, who usually goes by
car to the office, will drive on a certain routing of
roads and highways, and exactly this routing list of
streets will represent the configuration set for an
information query on traffic jams or other traffic
messages.
2.2 Automated Personalization with
Location-based Services
One very recent research topic is the application of
location-based services (Schiller, and Voisard 2004).
This could be used in the here described information
systems as well, since for the commuting sample,
the travel direction changes each day. Hence, the
direction represents also a parameter for the
information collection. Introducing the geographical
location into the information retrieval process,
allows the system automatically detecting the
travelling direction: When a commuting person is
inside or close by the office, the information system
knows implicitly, which station the next departure
place of the daily used train link will be.
Unfortunately, accessing this geographical
information in general will require additional high
efforts, for instance a GPS receiver inside the
handheld terminal. Theoretically, each cellular
phone terminal knows the communication cell,
where it is registered, and this cell, which is
identified by some kind of index value, could be
resolved into a geographical location. How such a
translation process can be implemented is discussed,
e.g., in (Roth, 2003). The inconvenience today in the
software structure of wireless devices is that this cell
broadcast content (its regularly broadcasted
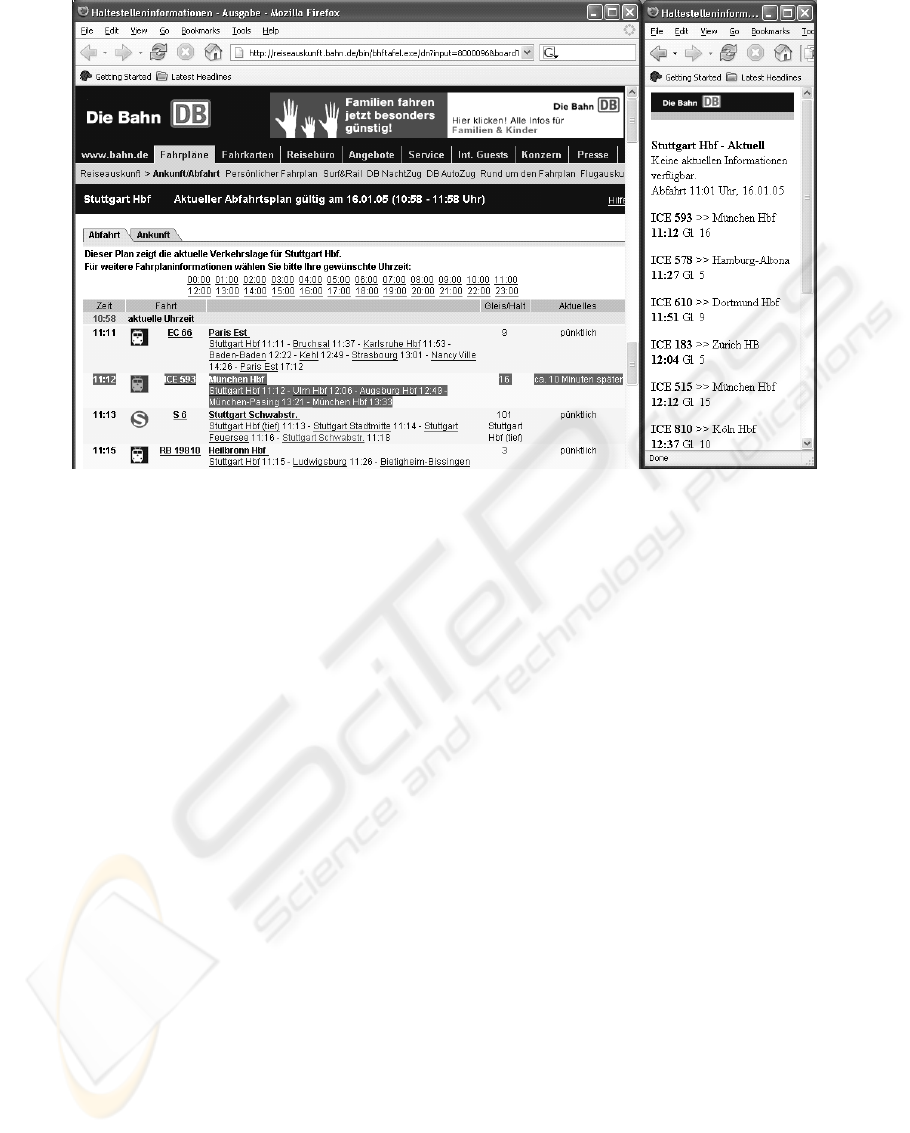
Figure 2: The railway company, which is used for the investigations, provides a Web site, from which departure
tables for all main stations can be downloaded (left browser frame). In parallel to that, also information pages for
WAP download are available, but the herein contained information is reduced for size reasons (right frame). Both
content pages were retrieved at the same time, and as seen in this sample, the WAP service also is not accurate,
because it does not report the information about the delayed train to Munich (“München”)
EFFICIENT INFORMATION ACCESS FROM CONSTRAINT WIRELESS TERMINALS - Exploiting Personalization
and Location-Based Services
225
information, which does not require any retrieval
costs) is not always accessible from add-on wireless
application software. The chance is that all cell
broadcast information will be available in future
through standardized APIs, and then the location-
based concepts can directly help to improve the
described information systems without introducing
new restrictions or requirements.
More recent communication technologies also
would allow location-based control of information
retrieval. Again for the commuting sample,
Bluetooth communication can be applied for
automatically determining the position of user: In
particular, when the user is inside the office, the fact
that the wearable device is registered in a local
Bluetooth communication cluster can be used as
location measure. For this, no application
communication with the wireless device is required,
but only the presence of the hand held terminal in
the Bluetooth cell has to be detected, which can be
done automatically and periodically from a host
computer inside the office. If the user enters during
the day once the office, this method provides already
a feasible indicator for switching the travelling
direction in the information system. As other
example, an e-mail forwarding concept was reported
already at a time (Weghorn, 2001), when
programming of handheld devices was not available
for cellular phones openly to the market. Today due
to the before described technologies and applicable
development systems like wireless JAVA
programming (Piroumian, 2002), also this
forwarding of important e-mail contents can be
automatically controlled by the before described
location detection mechanisms.
3 SAMPLE SYSTEM FOR TRAIN
DEPARTURE QUERYS
3.1 Information retrieval mechanism
After some prior concept design and simulation of
an information system on train actual departures, an
information access system was developed, which is
truly executable on JAVA-enabled wireless devices
(Piroumian, 2002). The intermediate agent is
implemented as JAVA servlet (Hall, and Parr 2001),
and it handles a query about a certain train
connection route. This tool uses a public Internet
page, which is operated by the railway company
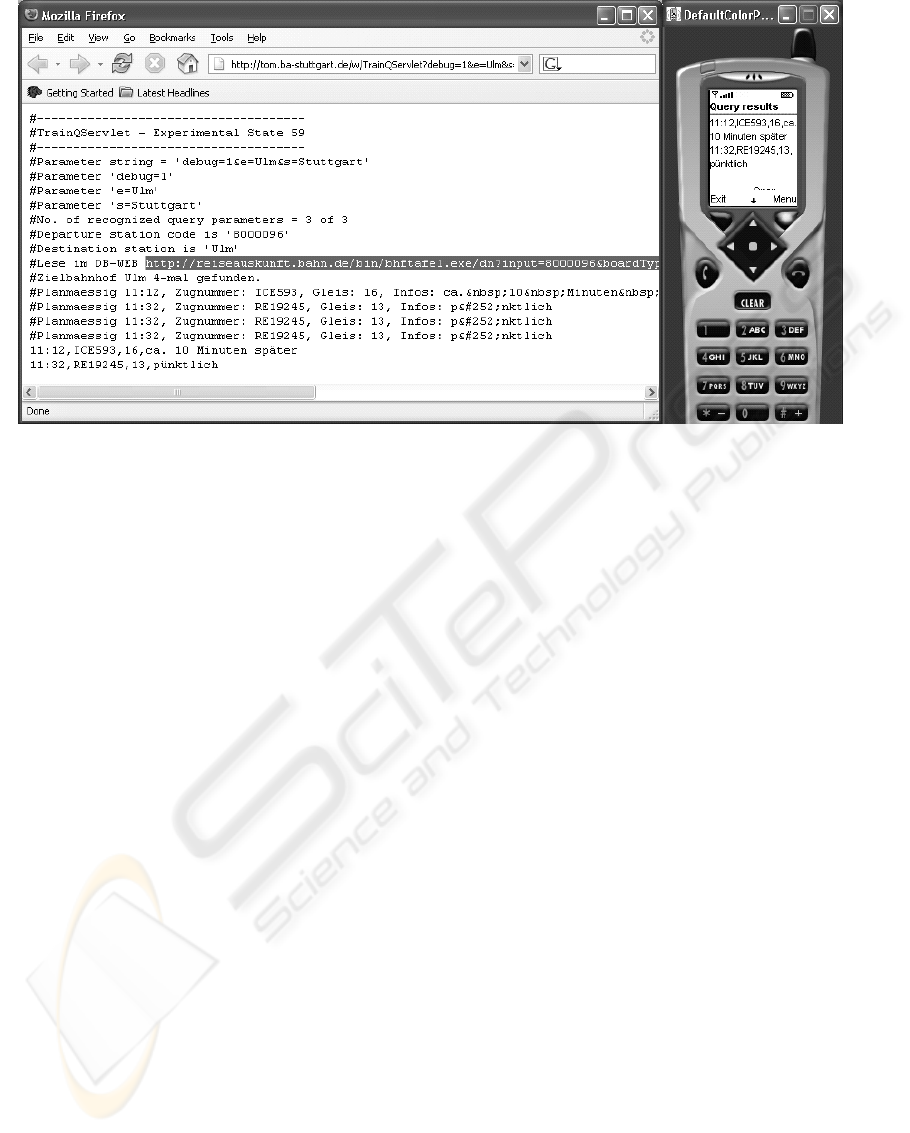
(Fig. 2), and translates the Web coded contents into
a format (Fig. 3) that is feasible for transfer and
display on a wireless terminal (Fig. 3). Depending
on the query parameters, the original information
source will have sizes of 300 kilobytes and more,
which obviously shows that a direct access to this
information by mobile browsing does not make any
sense. Truly, the same railway company operates a
WML page server for WAP access to the
information (Fig. 2), but the contents presented there
are only a fraction of the Web version; in particular,
if the reader doesn’t know the train code, the system
Figure 3: The personalized service filters all connections of interest out of the generalized Web departure table,
which is seen in Fig. 2. The debug mode of the mining agent (left browser frame) shows the intermediate steps of
this analysis, and the result will be displayed by the terminal software part (right frame) of the described
information system
WEBIST 2005 - WEB INTERFACES AND APPLICATIONS
226
is more or less worthless, because intermediate train
destinations are not displayed. For a personalized
application, the WAP solution provides the wrong
subset of information, at least for the indicative
sample of daily commuting. Another problem is that
it is obviously working incorrectly (Fig. 2), but this
is not a fundamental problem.
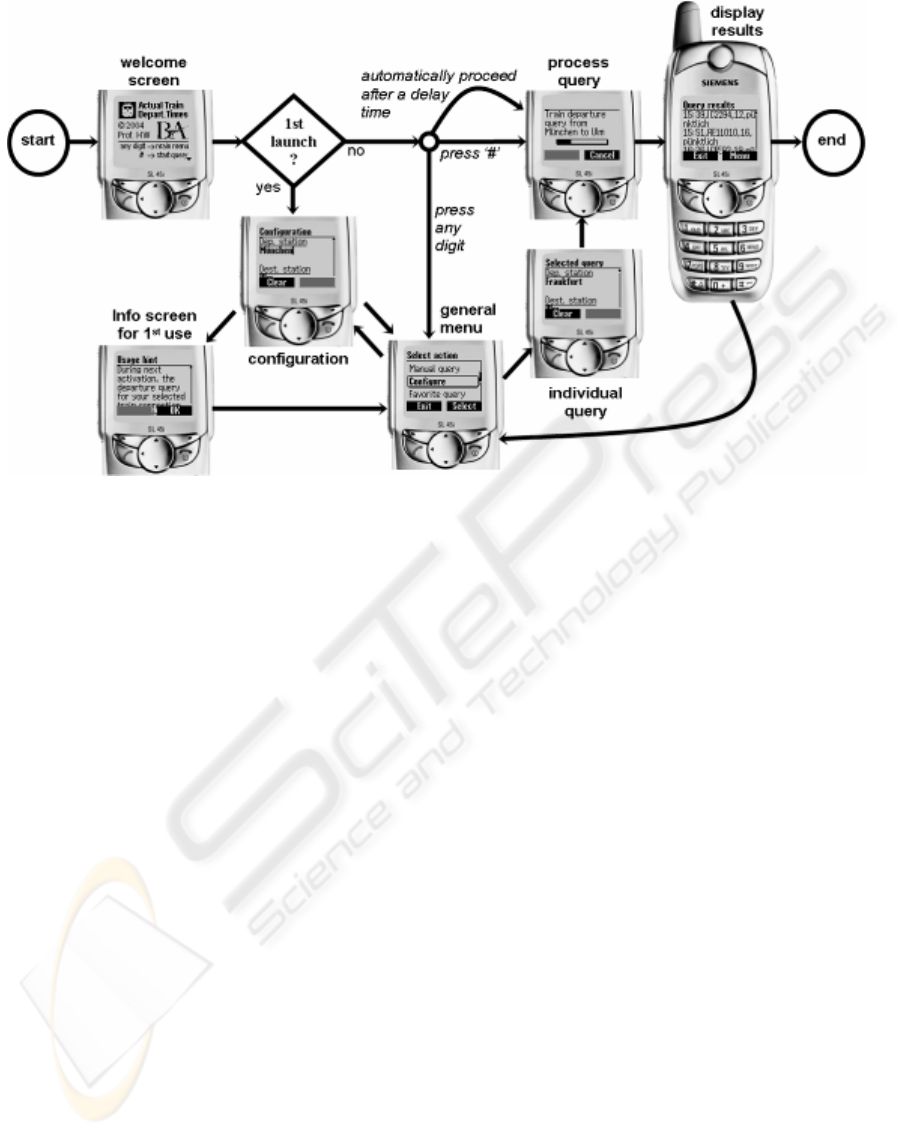
3.2 UI design for the terminal client
The minimization of required inputs is one aim for
the proposed information system. Therefore, the
normal operation mode in the train departure query
application is that after launching the terminal
software, the information retrieval will start
automatically. For overcoming the necessity of an
additional configuration tool, the train query
application starts with a welcome screen, which
dismisses after a defined short time delay (Fig. 4). If
the user doesn’t want to run the default query, the
welcome screen can be interrupted by a keyboard
press. In this case a selection menu will appear next,
and the user can modify the configuration for the
favourite query, or place a manual query. The latter
feature of performing individual queries shall make
the information system more flexible, and it can
casually be of interest, e.g., for use during business
travels. The first launch of the application after its
installation on the terminal requires one special
additional UI mode: During this, the customer is
informed about the regular behaviour of the
information tool, and is then directly switched to the
configuration menu.
The system was tested on six different physical
devices: First, a Palm IIIc PDA computer, and a
Siemens SL45i with B+W display screen belong to
the first generation of JAVA-enabled handheld
devices, which appeared on the market; next, the
devices Erricson T630, Erricson P900, Nokia 6600,
and Siemens SX-1 represent the recent generation on
the market, while the latter three smart phones are
based on the open operating system Symbian
(www.symbian.com). The implementation and the
tests showed that the different phone vendors do
have individual interpretations about the operation
of the standardized JAVA API. Therefore, several
adoptions were required to produce terminal
software, which is sufficiently working on all the
test devices, although the first implementation was
working cleanly in Sun’s simulation environment.
To give samples of this disturbing behaviour,
four of the devices do not display the defined
program icons, which would make the handling
more convenient for the non-technical user. Another
of the devices couldn’t display graphical images,
which were produced with standard UNIX imaging
tools. The alternatively used desktop software
produced images files, which were displayed
Figure 4: UI chart of the information channel on actual train departure times for a certain (personalized) travelling
route. The direction of travelling is determined by a configurable switching time. If the user doesn’t interfere, the
query process proceeds automatically through the direct path between the markers for “start” and “end”. This
sample shows that this kind of application is feasible for a use on simple-styled phones, which are equipped with
small B+W screens only
EFFICIENT INFORMATION ACCESS FROM CONSTRAINT WIRELESS TERMINALS - Exploiting Personalization
and Location-Based Services
227

correctly on all devices, but the coding length of
these images was bigger, which leads to a waste of
memory on the terminal.
For automatically determining the travelling
direction, an additional time parameter is defined
and used in the system. The user can set a time, e.g.
noon, from which the system assumes that the user
will travel home, which means that the departure and
the destination stations are exchanged for the
departure table query. This sample shows how the
requirement for knowing the geographical location
can be overcome. Although this doesn’t represent
always an accurate measure, it will in most cases be
a feasible strategy for replacing the detection of the
geographical location.
With the P900 smart phone it can be
demonstrated how convenient the use of the
proposed information tool can be, because on this
device JAVA applications can be placed for a quick
start on top menu level. The actions for running the
tool are opening first the keyboard cover, and next
pressing with the touch pen the appropriate icon.
Following this, the query launches automatically,
and the user can read after a few seconds delay the
result about the train connections of interest.
3.3 Performance measurements in
phone networks
The train information system was used with different
network operators and networking modes for
investigating the efficiency of the tool. In general, in
Europe data services can be used through the
wireless telephony network (GSM) as traditional
modem connection and with GPRS with enhanced
data communication. Understanding the tariffs of the
different network operators is not straight forward,
and hence the produced costs for the information
retrieval were also measured (Table 1).
In the standard GSM data link, the customer has
to pay for the time duration of the connection, while
with GPRS the customer has to pay theoretically for
the transferred data amount. The latter paying
method was too low for the network operators, and
they invented additional charges for GPRS, some are
billing an extra monthly charge of five Euros for
using GPRS, others bill for each day of use an
additional service charge (e.g. 19 Eurocents). This
all complicates the calculation, what the retrieval of
a dedicate information will cost, but exactly this
confusion may be of strategic business interest for
the network operators. As consequence, it is in
general not possible to specify the precise billing
amount for a single information access, e.g., one
retrieval on train departures.
In summary, it can be derived that running one
information query can in average cost down to 10
Eurocent with GPRS, while with the old modem
connection at least twice this amount is charged. The
required time for retrieving the information is an
important factor for the user handling. With the
GSM standard data link, the entire access will take
approximately one minute. With GPRS the overall
time depends on the fact, whether the mobile
terminal has already registered the GPRS link. In
this mode, most time is consumed for setting up the
data link (~ 15 sec), while the information transfer
from the application takes only a few seconds.
4 CONSIDERATION OF
EXPERIMENTAL RESULTS
4.1 Discussion of benefits for the
customer
For qualifying the benefit of the proposed
information access concept, its handling has to be
compared to alternative methods. Traditionally, one
could use a desktop computer with an Internet
connection or a phone voice service. Due to the
structure of current operating systems, the use of a
desktop computer will consume much more time,
because it has to be booted, the user has then to log
on to the operating system, and afterwards to launch
the Internet connection. After this, the information
retrieval can be invoked, and finally the whole
computer system has to be shut down. This will take
several minutes, and of course, the data terminal is
not wearable. With a laptop computer this process
can be accelerated, but in the end it will also take
considerably longer for accessing the information. In
addition to that, the laptop computer solution is not
conveniently applicable in many situations, e.g.
walking, going by public bus, or driving in a car.
With voice telephony services, it is like there is
no possibility of personalization. Hence, if the user
wants to obtain information about current train
departure, always a voice-controlled navigation
through an access tree will be required, which
consumes time and produces network costs. The
situation is comparable to Web browsing without
bookmark links. Summarizing, it can be stated that
the personalized access is much more efficient than
traditional alternatives, because it can be performed
in almost any situation and it will take one minute or
with the proper configuration only a fraction of a
minute. Each information access typically will cost
around 10 Eurocent, which may be more expensive
than with other systems.
WEBIST 2005 - WEB INTERFACES AND APPLICATIONS
228

4.2 Run-time behaviour of J2ME
devices
Besides the above-discussed difficulties with the
operation of J2ME standard UI elements, there arise
also problems with networking on the J2ME-enabled
devices manufactured by different companies. This
applies especially when using the standard GSM
data link instead of the enhanced GPRS mode. On
some devices, a network data link can be established
from the J2ME application, but it cannot be
terminated under application control. It is closed
down only after exiting the JAVA sub menu in the
phone UI. The consequence is that the user is
charged in background additional costs, e.g., when
the results of an information query are displayed,
although no data needs to be transferred any more.
Methods for closing down the physical layer
connection, which are available in the standard
JAVA system, are missing in J2ME. Interestingly,
this kind of operation is present in Sun’s sample
implementation for Palm OS handheld computers,
and it seems to be inherited by other devices. Even
worth appears the fact that some newer devices are
incapable at all of establishing a HTTP connection
with the standard data link. These devices are
working well with GPRS, but it depends on the
phone contract, whether GPRS mode is available.
For cost control reasons, and for reliability reasons
the recommendation for a non-technical customer
can only be using J2ME data networking only with
GPRS.
In general, the data networking configuration is
non-trivial, and therefore most devices are delivered
today with all possible configurations for the
different network operators. Unfortunately, it can be
observed that on some devices these settings
interfere with each other, and in the end there were
several cases detected, for which the data
networking was non-functional. After removing the
unusable configurations, these devices started
working correctly, but form this experience it can be
derived that also in GPRS mode non-expert
customers might be incapable of using the
information access software due to general
constraints of the device handling
4.3 SW engineering and XML coding
of contents
The original approach of the concept was that low
level coding (= binary exchange of information
contents) should improve the overall performance of
the wireless information system. From the
experiments (Table 1), it can be deducted that this is
not fully true, because in particular the transfer of
the content in the data communication consumes
only a small fraction of the overall access time.
Hence, coding the data packet according to
established software engineering philosophies (in
particular in XML: Bradley, 1998) would be
acceptable with GPRS for the transfer time and costs
as long as the content packet size remains in the
order of one kilobyte. Despite these measurement
results, there arises still some impact of inefficiency
on the terminal side, since XML coded contents will
require a more complicate parsing in the wireless
software part. Of course, this can be obtained by
using standard library packages (Setiawan, 2001),
but this will increase considerably the code size of
the handheld application.
On the other hand, thinking forward of PUSH
technologies (Ortiz, 2003), XML coding of contents
still is not recommended, because an SMS, which
can be used for this technology, will not be capable
of carrying that content size.
Table 1: Representative measurements of information access time and costs for different networking modes
Experiment
no.
Network
Operator
Mode Open URL Time for
content transfer
Costs Remarks
1 T-Mobile GPRS 9,2 sec 31 ms 19 ct
2 T-Mobile GPRS 3,5 sec <1 ms 19 ct
3.1 T-Mobile GPRS 16,28 sec
<1 ms
3.2 T-Mobile GPRS 3,00 sec <1 ms
3.3 T-Mobile GPRS 3,39 sec 15 ms
3.4 T-Mobile GPRS 3,44 sec 31 ms
28 ct
one
GPRS
session
4 Vodaphone
GSM std
22,25 sec
7564 ms 19 ct
5 Vodaphone
GSM std
17,56 sec
5377 ms 19 ct
6 Vodaphone
GSM std
20,96 sec
5146 ms 35 ct
7.1 T-Mobile GPRS 9,70 sec 31 ms
7.2 T-Mobile GPRS 3,11 sec <1 ms
28 ct
one GPRS
session
8.1 Vodaphone
GSM std
20,87 sec
6770 ms 35 ct
8.2 T-Mobile GPRS 3,47 sec <1 ms
n/a
8.3 T-Mobile GPRS 3,50 sec 140 ms n/a
performed
at the same
time
EFFICIENT INFORMATION ACCESS FROM CONSTRAINT WIRELESS TERMINALS - Exploiting Personalization
and Location-Based Services
229

5 CONCLUSION
A new information access system for truly mobile
access was conceptually designed and developed
during the recent years. In our former investigations
on this, the concept, which shall customers provide
an efficient and convenient access, was tested and
developed mainly on base of simulations. The
advance of the work presented here is the
application of the information retrieval system in
true networks under real conditions. On base of
these experiments, it can be derived that the claimed
properties, like increased access speed and improved
handling, can be achieved with the proposed kind of
information access structure.
Future work will stepwise regard quality of
information by means of AI, and it shall further aim
to reduce the information access costs, e.g. by
applying AI controlled proactive PUSH
mechanisms. Although the wireless JAVA platform
defines a standard API, the experience with true
devices is that it is not a straightforward task to
develop applications, which are running truly
sufficiently on all devices. Extra effort is required
for achieving this, and therefore alternative
technologies, e.g. C++-based software on Symbian
devices, shall be investigated in future for obtaining
best overall performance.
Also the application fields shall be expanded.
Besides information on public transportation and car
traffic, we are working in actual projects on weather
channels for a customized retrieval of local recent
information and forecasts. Furthermore, we are
currently investigating how Web service technology
(Aleksy and Gitzel, 2004) can contribute to an
improvement of the described information access
systems.
REFERENCES
Aleksy, M., and Gitzel, R. (eds), 2004, Workshop on Web
Applications and Middleware (WAM2004). In GI-
Edition Lecture Notes in Informatics(LNI) -
Proceedings, Köllen Druck+Verlag GmbH, Bonn,
Germany, pp 264-286.
Bradley, N., 1998. The XML Companion, Addison-
Wesley. Harlow, 1
st
edition.
Hall, M., and Parr, M., 2001. Core Servlets and JAVA
Server Pages. Sun Microsystems Press, Prentice Hall
PTR. Dorchester, 2
nd
edition.
Johnson, P., 1998. Usability and Mobility: Interactions on
the move. In First Workshop on Human Computer
Interaction with Mobile Devices, Glasgow, May 1998.
GIST Technical Report G98-1. Department of
Computing Science, University of Glasgow.
Mahmoud, Q. H., 2002. Accessing and using Internet
services from JAVA-enabled handheld wireless
devices. In Braz, J., et al. (eds), 4
th
International
Conference on Enterprise Information Systems,
Ciudad Real, April 2002. ICEIS Press.
Ortiz, E., 2003. The MIDP 2.0 Push Registry.
http://wireless.java.sun.com/midp/articles/pushreg/,
February 2003.
Piroumian, V., 2002. Wireless J2ME Platform
Programming, Prentice Hall. Palo Alto, 1
st
edition.
Riezenman, M. J., 2002. The ABCs of IEEE 802.11.
IEEE Spectrum Online, September 2002.
http://www.spectrum.ieee.org/WEBONLY/resource/se
p02/802ABCs.html
Roth, J., 2003. Flexible Positioning For Location-Based
Services. IADIS International JournalWWW/Internet,
Vol. 1, No. 2, pp 18-32.
Schiller, J., and Voisard, A. (eds), 2004, Location-Based
Services. Morgan Kaufmann Publishers, San
Francisco, USA.
Setiawan, T., 2001. The Use of J2ME with a Campus
Portal for Wireless Devices, Master Thesis, Faculty of
Engineering, San Jose State University. San Jose,
USA.
Wang, F., et al., 2003. An E-Commerce System
Integrating Data Mining Functionalities. In Palma dos
Reis, A., and Isaías, P. (eds), e-Society 2003, Lisbon,
June 2003. IADIS Press.
Weghorn, H., 2001. Notification and routing of electronic
mail to mobile phone devices. In Miranda, P., et al.
(eds), 2
nd
International Conference on Enterprise
Information Systems, Setúbal, July 2001. ICEIS Press.
Weghorn, H., 2003. Teaching Wireless JAVA at the
University of Cooperative Education. In Mahmoud, Q.
H. (ed), 2
nd
International Workshop on Wireless
Information Systems WIS 2003, Angers, April 2003.
ICEIS Workshop Proceedings.
Weghorn, H., 2004-1. In Isaías, P., et al. (eds), IADIS
International Conference on e-Society 2004, Vol. I,
Avila, July 2004. IADIS Press.
Weghorn, H., 2004-2. Employing the C2C Principle for
Making the Use of Data Services on Mobile Phones
More Attractive. In Ascenso, J., et al. (eds), 1
st
International Conference on E-Business and
Telecommunication Networks, Vol. 3, Setúbal, August
2004. ICEIS Press.
WEBIST 2005 - WEB INTERFACES AND APPLICATIONS
230
